- file name: AIKASM.exe
- packer: ASProtect 1.23 RC4
- tools:
-OllyDbg with OllyDump, aadp4olly plugins-Import REConstructor @ ImpREC-LordPE- this tutorial was derived from site
- credit: +Neffarion
i. setting up OllyDbg
ii. setting up aadp4olly plugin
1a.-open OllyDbg and load AIKASM.exe-click 'No' to skip analyzing compressed code
1b.-press [Shift]+[F9] 16 times until you reach the code shown in the picture below
Spoiler
*[Shift]+[F9] x-times is what a reverse engineers call 'exception counting trick'
*load the program into OllyDbg
*n = count how many times [Shift]+[F9] is pressed untill the program freely runs
*restart the program in OllyDbg
*x = n-1
**this is just an additional information, this is not one of the steps in the tutorial
-toggle a Breakpoint (BP) on the first RETN at [0x2E43A29 ] and click 'Yes' in the warning box
1c.-press [Shift]+[F9] once more to break on the BP
1d.-press [Alt]+[M] to bring up the 'Memory map' window-right click on AIKASM-code line and select 'Set memory breakpoint on access'
1e.-press [F9] and take note of the address where the run command landed, it is the 'Entry Point(EP)'
1f.-scroll up the code a bit until you see a recurrences of a single instruction such as shown below
-press [Ctrl]+[A] to analyze the codes
2a.-restart AIKASM.exe in OllyDbg or you can press [Ctrl]+[F2]-click 'No' to skip analyzing compressed code
2b.-repeat the steps from 1b until 1d
2c.-press [Ctrl]+[T] to bring up the 'Set Condition' dialog and configure it as shown below-click 'OK'
-press [Ctrl]+[F11]
2d.-go to 'View' and select 'Run trace'-right click anywhere within the 'Run trace' window and select 'Highlight register' and select 'EBP'
-scroll down to the bottom of the 'Run trace' window until a highlighted 'EBP=[0x12FFC0]' is seen-take note of the address prior to the highlighted EBP register, it is the beginning of the stolen bytes
2e.-write down the instructions from [0x2E5620D] to [0x2E5626C], leave out all the 'JMP SHORTs' and red-marked instructions
0x2E5620D PUSH EBP0x2E5620E MOV EBP,ESP0x2E56210 PUSH -10x2E56212 PUSH 6247100x2E56217 PUSH 5EF7180x2E5621C MOV EAX,DWORD PTR FS:[0]
0x2E5622F PUSH EAX0x2E56230 MOV DWORD PTR FS:[0], ESP0x2E56237 SUB ESP, 580x2E56247 PUSH EBX0x2E56255 PUSH ESI0x2E56263 PUSH EDI0x2E56264 MOV DWORD PTR SS:[EBP-18], ESP
-observe the instructions in the above figure and you will notice that the stolen bytes stopped before a 'PUSH (EP)'-(credit to fennes for verifying the correct stolen bytes)
3a.-restart AIKASM.exe in OllyDbg or you can press [Ctrl]+[F2]-click 'No' to skip analyzing compressed code-repeat the steps from 1b until 1f-right click on the start of the CodeCave/OEP [0x5EE833] and select 'New origin here'
3b.-go to 'Plugins' and select 'OllyDump' and select 'Dump debugged process'-configure the 'OllyDump' dialog as shown in the picture below
-make certain that the 'Modify:' field is correct:
= [EP - BaseAddress]= [0x5EE833] - [0x400000]= [0x1EE833]
-click 'Dump'
3c.-while 'OllyDbg' is still open, launch 'ImportREC'-select 'AIKASM.exe' process from the drop down list
3d.-change the 'OEP' field to the one calculated previously-click 'IAT AutoSearch' and click 'OK' in the next dialog
3f.-change the 'Size' field to [0x1000] and click 'Get Imports'
3g.-click 'Show Invalid'-right click on any of the highlighted invalid function and select 'Trace Level1(Disasm)'
3h.-click 'Show Invalid'-right click on any of the highlighted invalid function and select 'Plugin Tracers' and select 'ASProtect 1.23 rc4'
3i.-click 'Show Invalid'-right click on any of the highlighted invalid function and select 'Delete thunk(s)'
3j.-click 'Fix Dump'-select 'dump.exe' and click 'Open'
-a new file named 'dump_.exe' should now be created in the AikaSEA folder-close 'ImpREC'
4a.-close 'AIKASM.exe' process in 'OllyDbg' and open 'dump_.exe'
4b.-select the entire instructions from [0x5EE833] to [0x5EE857] which is the codeCave, right click on any of it and select 'Assemble'
-replace the whole instructions with the copied instructions previously in step 2e
before replacements
after replacements
4c.-press [Ctrl]+[A]-right click anywhere within the 'CPU' window and select 'Copy to executable' and select 'All modifications'
-click 'Copy All' in the next dialog
-close the newly popped up window by clicking the 'X' icon at the top right corner
-click 'Yes' to save the modified file to disk
-in the 'Save file as' window, select 'dump_.exe' and click 'Save'-click 'Yes' to overwrite files
5a.-open 'LordPE' and click 'Rebuild PE'
-select 'dump_.exe' and click 'Open'-click 'OK' in 'LordPE' window
have fun..
Results 1 to 10 of 79
-
2012-01-05, 03:20 PM #1
AikaSEA ASProtect manual unpacking
Last edited by S4R4H; 2012-02-05 at 08:29 PM. Reason: updated.for.AikaSEA.ver.140
I like to make stupid theories and asssumptions..
-
-
-
2012-01-05, 03:57 PM #2Member-in-trainingUlquiorra



- Join Date
- 2010 Dec
- Location
- brasil MG
- Posts
- 74
- Thanks

- 21
- Thanks

- 183
- Thanked in
- 30 Posts
- Rep Power
- 0
good tutorial
put some images from the configuration ollybdg
to get better
-
2012-01-05, 05:05 PM #3
-
2012-01-06, 03:35 AM #4
Wow Thanks a Lot S4R4H,
Your Guide Really Help Me...
Last Time I Stuck At Stolen Byte And ImpRec..
But Now I Can Unpack Without Error.
Goood Job.
-
2012-01-06, 11:12 AM #5New membercraco28


- Join Date
- 2011 Dec
- Posts
- 6
- Thanks

- 5
- Thanks

- 0
- Thanked in
- 0 Posts
- Rep Power
- 0
i wanna try this but can you give me an idea whats the purpose of this?? its bypass or what?
-
2012-01-06, 11:36 AM #6New memberloveisover


- Join Date
- 2012 Jan
- Posts
- 10
- Thanks

- 0
- Thanks

- 0
- Thanked in
- 0 Posts
- Rep Power
- 0
how to set up aadp4olly plugin?
-
2012-01-06, 12:33 PM #7
if i can try this way with aikain.exe?
or different aika version have different ways?
-
2012-01-07, 04:21 AM #8New member[iTF]Tanker
![[iTF]Tanker is offline](https://progamercity.net/images/styles/pgcsilver/statusicon/user-offline.png)

- Join Date
- 2010 Nov
- Posts
- 21
- Thanks

- 24
- Thanks

- 38
- Thanked in
- 2 Posts
- Rep Power
- 0
@S4R4H :
Thanks for very helpful tutorial.
I have followed all your tutorial, but stuck in that find stolen bytes.
I can't find any code like your picture.

I only found two similar code, see the figure below.
Can you help me ? Thank you very much.Please register or login to download attachments.
-
2012-01-07, 06:04 AM #9New memberloveisover


- Join Date
- 2012 Jan
- Posts
- 10
- Thanks

- 0
- Thanks

- 0
- Thanked in
- 0 Posts
- Rep Power
- 0
I dunno where to find out the version of your OllyDbg with OllyDump and aadp4olly plugins.
Can someone help me?
-
2012-01-08, 04:43 PM #10
it is not a bypass.. the guide is meant to 'fix' the client for further analyzing..
originally the client that you download and install is protected with a software protector, ASProtect..
its job is to shield the client from being reverse engineered..
ASProtect accomplish its goal by
- mangling the OEP
- module calls are obfuscated (functions are replaced with JMP's)
- ASProtect takes a certain amount of bytes from the original program and relocates them
gameguard bypass is what come after the decompression, you have to learn how to do that yourself..
OllyDbg download link: odbg110.zip
OllyDbg OllyDump plugin: OllyDump
OllyDbg aadp4olly plugin: aadp4olly
dump all the plugin files into OllyDbg folder..
there are 2 places where 'EBP' register is highlighted, yours is the first occurrence..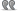 Originally Posted by [iTF
Originally Posted by [iTF
scroll down until you reach the bottom of the 'Run trace' log, you will see a highlighted 'EBP=[0x12FFC0]', that is where your stolen bytes are located..Last edited by S4R4H; 2012-01-08 at 05:09 PM.
I like to make stupid theories and asssumptions..
-
The Following User Says Thank You to S4R4H For This Useful Post:
Similar Threads
-
[Info] Manual Patching, patch info
By Dwar in forum Requiem OnlineReplies: 25Last Post: 2018-11-06, 02:37 PM -
[Dev] Cabal EU Yoda-ASProtect Unpacked
By Grooguz in forum Cabal Bots, Hacks, CheatsReplies: 8Last Post: 2013-05-31, 01:31 PM -
GameShield Manual Unpacking and Modifying Licenses
By h4x0r in forum Anti-Cheat SystemsReplies: 0Last Post: 2011-10-12, 10:13 PM -
[Info] Dragon Nest CN manual unpacking zip archive
By Dwar in forum Other MMOReplies: 0Last Post: 2011-06-29, 06:12 AM -
[Info] ARGO Online manual updating
By Dwar in forum Other MMOReplies: 0Last Post: 2011-06-12, 09:22 AM































 Reply With Quote
Reply With Quote
